Sofacy (aka APT28, Fancy Bear and Tsar Team) is a highly active and prolific cyber-espionage group. Overview of Sofacy activities in 2017, revealing a gradual moved away from NATO-related targets at the start of 2017, towards targets in the Middle East, Central Asia and beyond. Sofacy uses spear-phishing and watering-hole attacks to steal information, including account credentials, sensitive communications and documents. This threat actor also makes use of zero-day vulnerabilities to deploy its malware.
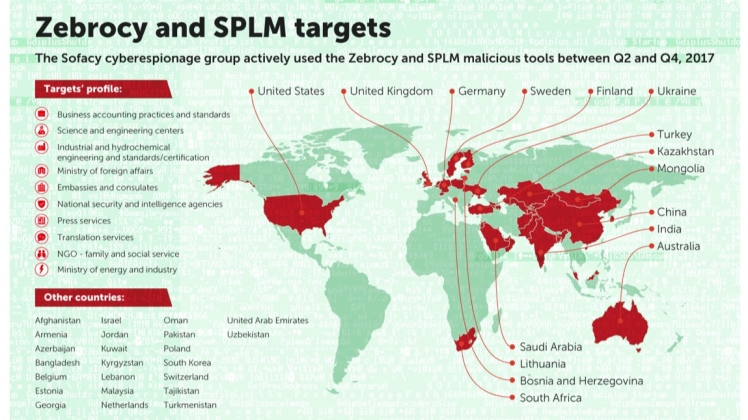
Sofacy uses different tools for different target profiles. Early in 2017, the group’s ‘Dealer’s Choice’ campaign was used to target military and diplomatic organizations (mainly in NATO countries and Ukraine).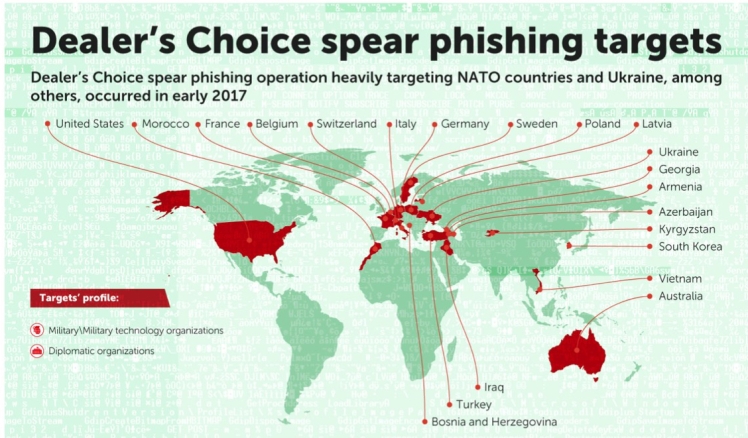 Later in the year, the group used other tools from its arsenal, ‘Zebrocy’ and ‘SPLM’, to target a broader range of organizations, including science and engineering centers and press services, with more of a focus on Central Asia and the Far East.
Later in the year, the group used other tools from its arsenal, ‘Zebrocy’ and ‘SPLM’, to target a broader range of organizations, including science and engineering centers and press services, with more of a focus on Central Asia and the Far East.
Sophisticated threat actors such as Sofacy continually develop the tools they use. The group maintains a high level of operational security and focuses on making its malware hard to detect. In the case of groups such as Sofacy, once any signs of their activity have been found in a network, it’s important to review logins and unusual administrator access on systems, thoroughly scan and sandbox incoming attachments, and maintain two-factor authentication for services such as e-mail and VPN access.
Sofacy’s Zebrocy malware has competed for access to victim’s computers with the Russian-speaking Mosquito Turla clusters; and where its SPLM backdoor has competed with the traditional Turla and Chinese-speaking Danti attacks. The shared targets included government administration, technology, science and military-related organizations in or from Central Asia.
The most intriguing overlap is probably that between Sofacy and the English-speaking threat actor behind The Lamberts. The connection was discovered after researchers detected the presence of Sofacy on a server that threat intelligence had previously identified as compromised by Grey Lambert malware. The server belongs to a Chinese conglomerate that designs and manufactures aerospace and air defense technologies. However, in this case the original SPLM delivery vector remains unknown. This raises a number of hypothetical possibilities, including the fact that Sofacy could be using a new and as yet undetected exploit or a new strain of its backdoor, or that Sofacy somehow managed to harness Grey Lambert’s communication channels to download its malware. It could even be a false flag, planted during the previous Lambert infection. We think that the most likely answer is that an unknown new PowerShell script or legitimate but vulnerable web app was exploited to load and execute the SPLM code.
#BSG